Cyber security isn’t just a media buzzword, or a priority for IT professionals, it has become a real concern for everyone who has an e-mail account, banks online or uses a credit card. On a larger scale, recent events have shown that industry too is not only susceptible to cyber crime, but could also be a favorite new target. Fluid handling professionals play an important role in keeping vital industrial systems operating properly and safely. Whether for oil & gas, water treatment, chemical processing, or power generation, this includes ensuring plant Supervisory Control and Data Acquisition (SCADA) Systems are secure.
When it comes to cyber security in process control, SCADA can be misleading. Nearly all of the process control systems today, including PLCs, SIS, DCS, and so on, use Ethernet and TCP/IP for their communications. They also use or connect to COTS (Commercial-Off-The-Shelf) technology like USBs and the Windows operating system. Even flowmeters today can be purchased with Ethernet interfaces. All of these factors make systems vulnerable to some form of cyber event, whether deliberate, like the Stuxnet attack that crippled centrifuges at a nuclear plant in Iran in 2010, or accidental, like the shutting down of cooling water controllers at Browns Ferry Nuclear plant in 2006.
In order to ensure the reliability of any system, experts say fluid handling engineers need to factor in cyber security. “Fluid handling engineers need to implement good cyber security practices in order to ensure high availability and reliability of their systems,” says SCADA security expert Eric Byres, CTO and VP Engineering of Tofino Security, part of Belden’s Hirschmann industrial networking group. “They can’t think that SCADA does not apply to them. Indeed, virtually all process control systems today use Ethernet, TCP/IP and COTS technologies, making them vulnerable to cyber events.”
Major Trends in SCADA Security
Byres has seen several major trends in SCADA security over the last five to 10 years that deal with the convergence of company networks and industrial technologies. Traditionally, companies developed distributed control systems (DCS) and SCADA systems that were separated from other corporate systems. Today, many control systems have become accessible through non-SCADA networks due to the demand for real-time operational data and the demand for support access. The business demand to make control networks more accessible to a wider range of users proves to be cost-effective, but also comes with the potential risk of making the control system more vulnerable to viruses, worms and hackers. Some of the trends Byres sees are the shift from enterprise to industrial network connections, the use of COTS systems, and the adoption of TCP/IP networking technology.
- Enterprise to Industrial Network Connections. Businesses want real-time data to enhance performance and are connecting their network to the network on the plant floor to get it. The result is increased cyber security risk.
- COTS—Commercial-Off-The-Shelf-Technology. Industry has been adopting standard equipment such as Windows workstations instead of proprietary equipment as in the past. While there are still many industrial-specific technologies being used, the adoption of COTS has been compelling due to reduced costs. Again, the result is increased cyber security risk.
- TCP/IP—Transmission Control Protocol/Internet Protocol. Similarly, the adoption of TCP/IP as a networking technology saves money, but can expose industrial networks to more cyber ?security risks.
Stuxnet & SCADA
Along with new technology shifts, the computer worm Stuxnet set off another trend in the security community. Byres describes Stuxnet as a “game changer that awakened the hacker and ‘security researcher’ community to how easy it is to cause damage to industrial systems.” Dubbed as a “super cyber weapon,” Stuxnet was the first malware to specifically target an industrial process. It was designed to attack Siemens PCS7, S7 PLC and WinCC systems and was successful in infiltrating thousands of computers around the world.
Knowledgeable security experts had been advising and warning about SCADA security concerns for more than 10 years, and certainly more strongly since 9/11. However, management and the public largely ignored concerns until Stuxnet, says Frank Dickman, an engineering and technical consultant to leading data communications firms. “It was a wake-up call demonstrating that earlier warnings were not just hot air,” he says. “Stuxnet took the idea of ‘hacking’ to a new definition—It is no longer some disenfranchised teenager hacking away in his bedroom. Hacking is the current province of criminal organizations, nation states, foreign competitors, and terrorists.”
Dickman points out there were industrial security products on the market that were capable of detecting and blocking Stuxnet, or other advanced persistent threats, prior to the initial discovery of Stuxnet. For example, he points to the mGuard product by Phoenix Contact.
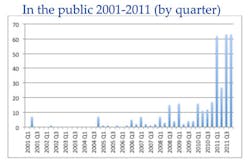
In its wake, Stuxnet left a blueprint for cyber war and a heightened awareness of both the need for more robust cyber security and the increased risks faced by industrial facilities. With this came the trend of vulnerability disclosures. Ever since Stuxnet, security researchers have been busily releasing vulnerability disclosures for industrial equipment, complete with exploit code, which can now be purchased on the Internet. According to a presentation by Critical Intelligence’s Sean McBride, The ‘Lost’ Decade: An Empirical Analysis of ICS-Specific Vulnerabilities since 2001, 215 ICS vulnerabilities were made public in 2011. That number accounts for more public disclosure of vulnerabilities than in the previous decade. Furthermore, the publicly disclosed vulnerabilities are only a fraction of what exist, Byres says.
Source: “Documenting the ‘Lost Decade’—An empirical analysis of publicly disclosed ICS vulnerabilities since 2001,” by Sean McBride, Critical Intelligence
Key Threats to SCADA Systems
While Stuxnet is known as the first cyber attack to target an industrial process, it will certainly not be the last. And threats among non-industrial sectors to date, are now becoming threats to industry, even if in less obvious ways. Some of those concerns, according to Byres, include Advanced Persistent Threats (APTS), malware, and “spear-phishing.”
- Advanced Persistent Threats (APTs), such as the complex worm known as Flame, are focused on industrial espionage and aim to steal business information rather than disrupt processes. They are hard to detect, they can hide and collect data for years, and the losses resulting from them are financial and reputation-related rather than safety or environmental incidents. These types of threats have been used to attack the financial sector in the past, but now they are attacking industry too.
- Malware not aimed at the plant can still be costly due to losses in manpower resources and expenses to eliminate it. For example, Stuxnet was aimed at a uranium enrichment plant, but it infected thousands of computers around the world. Once it was made public, it cost the “bystander” companies millions of dollars to eliminate it from their systems.
- “Spear Phishing” attacks. In the last two years both the United States and Canadian governments have announced that their employees have received e-mails that seem to come from trusted sources, asking them to download or access something, leading to the installation or spread of malware in government systems.
Protection Through Standards
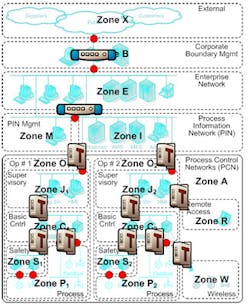
Some ways industry is reacting to cyber security threats in general is with new technology and through new standards and certifications. Byres recommends the ISA IEC 62443 standard, which originated with the International Society of Automation (ISA), and has been internationally endorsed through the International Electrotechnical Commission (IEC). It advises companies to use a “zone and conduit” model of dividing up their network into zones of devices with similar security requirements. Conduits between zones regulate the access to the devices in the zone. This model is often a more realistic and cost-effective method of providing cyber security than trying to secure legacy equipment itself, Byres says. Major oil and gas and chemical companies, such as Exxon, Dow and DuPont are using this standard. “The ISA IEC 62443 standard provides an excellent starting point and guidance for building IACS (Industrial Automation & Control System) cyber protection programs,” Byres says.
Oil and gas refinery network segmented into zones as per the ISA IEC 62443 standard. Conduits connect the zones and are secured using designed-for-industry firewalls.
Image courtesy of Tofino Security
A newer certification on the market is ISA Secure, which a number of major vendors in flow and process control are moving toward, Byres says. Honeywell was one of the first, announcing in June 2011 that its Honeywell Safety Manager (a Safety Integrated System or SIS control system) achieved ISA Secure Level 1 certification. ISA Secure certification is based on a rigorous security validation process that starts with a Communications Robustness Test (CRT) assessment phase, followed by two more assessment phases, the Functional Security Assessment (FSA) and the Software Development Security Assessment (SDSA). According to Byres, the additional second and third assessments are where real progress in ICS and SCADA security will be found “because they consider the underlying design, development practices and vendor-recommended deployment of the product, rather than just whether it stands up to some bad traffic,” Byres wrote in a Tofino blog post in 2011.
New Security Solutions for Industry
SCADA security products are also undergoing a transformation. Until recently, security products have been designed largely for the needs of IT personnel and enterprise applications, not for control engineers and industrial control systems. But now a number of new products, such as the Honeywell Modbus TCP Firewall and the Tofino Industrial Security Solution, have been specifically designed to secure highly critical control systems. Unlike IT-focused security products, new products have been developed with the environment and requirements of the process control world in mind. They are specially engineered to handle harsh operating environments and support industrial communications protocols. Further, new industrial security products can be installed, configured, and updated without having to shut down the control network.
“At the present time, as it has been for several decades, IT professionals have been largely uninvolved with SCADA control systems,” Dickman says. “SCADA systems remain the responsibility of engineering and production personnel. As a result, it is imperative that engineers familiar with SCADA be involved in implementing the security and protection of these systems while coordinating with and educating IT.”
5 Key SCADA Security Resources & Trainings
1. Tofino Security Blog: www.tofinosecurity.com/blog.
2. United States Computer Emergency Readiness Team (US-CERT): www.us-cert.gov/alerts-and-tips.
3. National SCADA Test Bed (NSTB) Advanced Training: www.inl.gov/scada/
4. SCADAhacker.com: cyber security training, ICS (DS/SCADA) security services, and security research and development at www.scadahacker.com.
5. Exida: cyber security certification, training, software, resources, and more at www.exida.com.
Securing the Future
Looking ahead into a future where cyber security issues will firmly remain, experts see “perimeter defense” models for securing SCADA systems—strong on the outside, but vulnerable on the inside—falling to the wayside in favor of multiple-point security. Today, sophisticated companies are already choosing “defense-in-depth” strategies that include zones that allow security problems to be contained in small areas rather than spread throughout a plant. In the future, smart facilities will take on layered strategies in which networks, control devices, and control systems are individually and collectively secured.
Going forward, Byres sees technology solutions continuing to move toward more industry-focused solutions. IT firewalls that protect against things like mail and http breaches don’t apply in industrial settings. Now there are solutions for industrial-specific protocols like OPC and Modbus. These solutions also use advanced techniques like Deep Packet Inspection (DPI), a deeper investigation of communications, and deployment of rules that takes place after traditional firewall rules have been applied.
“In the future, SCADA systems will be better protected through increased application of defense in depth strategies, including use of the ISA IEC 62443 zone and conduit model, and through the application of technology solutions that are designed from the ground up for industrial requirements,” Byres says.
Amy W. Richardson is the managing editor of Flow Control magazine. Contact her at [email protected].